Editorial
A Decade of Shaping Sweden’s Cybersecurity Future
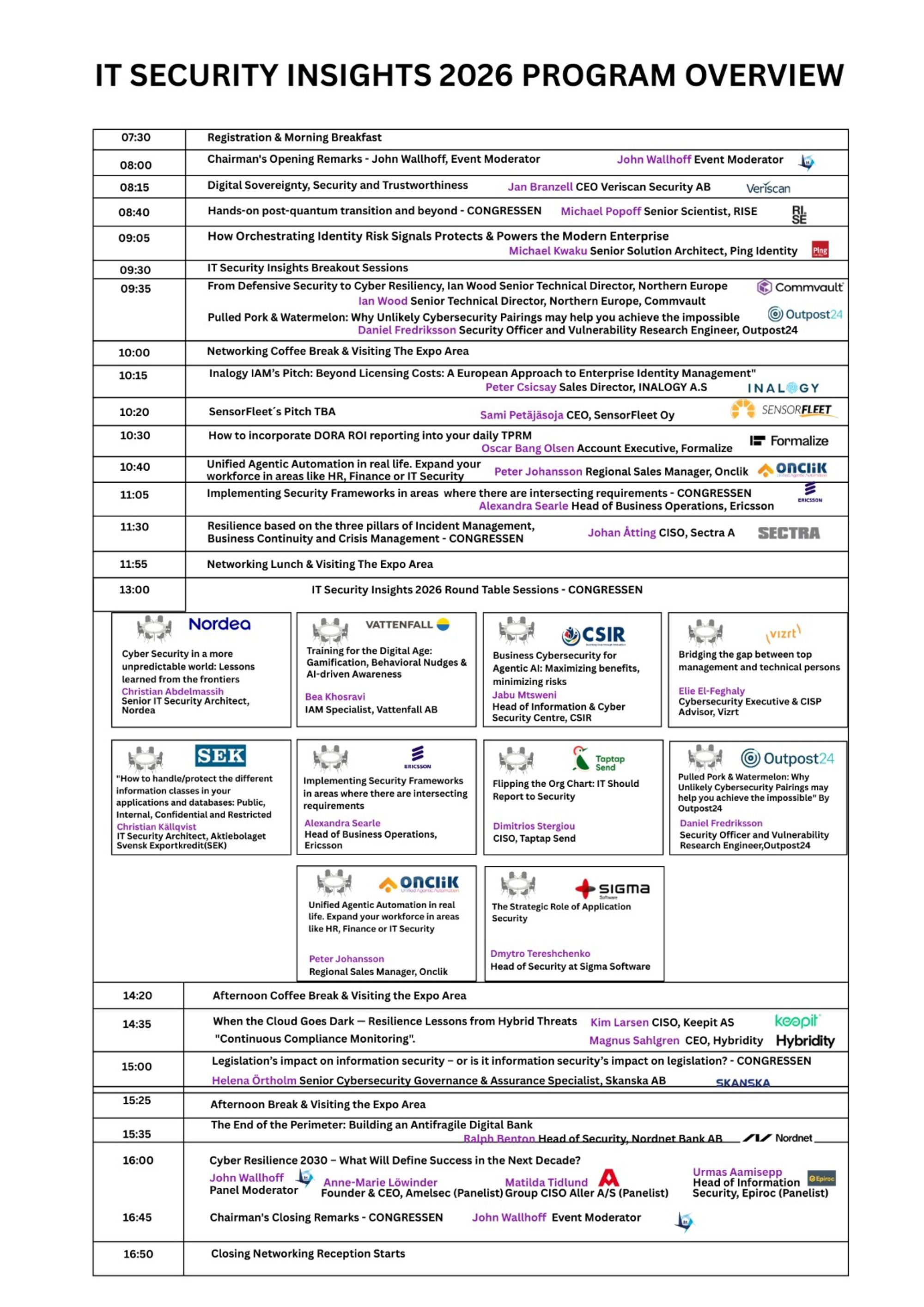
For the past ten years, the IT Security Insights Conference has been more than just an event — it has been a meeting ground for the brightest minds and strongest voices in Sweden’s cybersecurity landscape. As we step into our 10th Edition, we reflect on a decade of progress while looking ahead to the pressing challenges that will define the next era of digital security.
Cybersecurity today is not just a technical issue; it is a strategic imperative that affects every layer of an organisation. Medium to large enterprises in Sweden and across the globe are navigating an increasingly complex environment — balancing innovation, regulation, and resilience against a backdrop of ever-evolving threats. This year’s programme is designed to equip leaders with clarity and direction, combining visionary keynotes, real-world case studies, interactive panels, and sector-focused workshops.
But what truly defines IT Security Insights is its community. Over the years, we’ve seen leaders — CISOs, CIOs, CTOs, heads of IT, and compliance experts — come together not just to share knowledge, but to build partnerships that last beyond the conference walls. It is this spirit of collaboration that transforms discussions into action and ideas into innovation.
As we celebrate this milestone edition, our mission remains unchanged: to inspire, connect, and empower the professionals shaping the future of cybersecurity. We invite you to join us, not only to mark a decade of achievement, but to be part of the conversations that will drive the next decade of resilience and growth.
Registration is now open — and so is the next chapter of Sweden’s cybersecurity story.
We are looking forward to seeing you on the 4th of March, 2025 at Hotel Birger Jarl!
Sincerely,
Robert Kitunzi
Event Project Manager